The WordPress Security Scanner WPScan’s 2024 WordPress Vulnerability Report draws attention to WordPress vulnerability trends and suggests the kinds of things website publishers (and SEOs) should be aware of ).
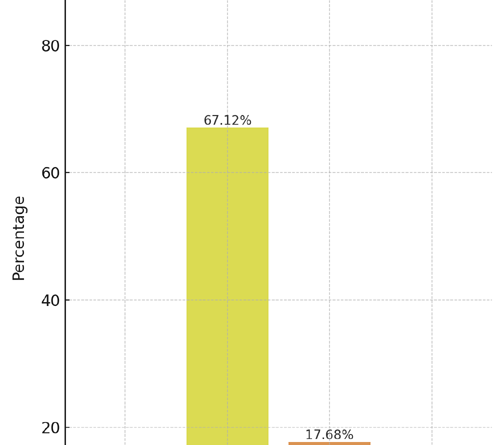
Some of the report’s key findings were that just over 20% of vulnerabilities were classified as high or critical threats, with medium severity threats at 67% of reported vulnerabilities, representing the majority Many consider medium-level vulnerabilities to be low-level threats, but they are not and should be considered worthy of attention.
The WPScan report stated:
“While severity does not directly translate to exploit risk, it is an important guideline for website owners to make an informed decision about when to disable or update the extension.”
WordPress Vulnerability Severity Distribution
Critical-level vulnerabilities, the highest level of threat, accounted for only 2.38% of vulnerabilities, which is (essentially) good news for WordPress publishers. However, as mentioned above , when combined with high-level threat percentages (17.68%) the number of worrisome vulnerabilities rises to almost 20%.
Here are the percentages by severity classification:
Critical 2.38% Low 12.83% High 17.68% Medium 67.12%
Authenticated vs. Unauthenticated
Authenticated vulnerabilities are those that require an attacker to first attain the user’s credentials and corresponding permission levels in order to exploit a particular vulnerability. Exploits that require subscriber-level authentication are the most exploitable of the authenticated exploits, and those that require admin-level access present the lowest risk (although not always low risk for various reasons).
Unauthenticated attacks are generally the easiest to exploit because anyone can launch an attack without having to first acquire a user credential.
WPScan’s vulnerability report found that about 22% of reported vulnerabilities required either subscriber level or no authentication, representing the most exploitable vulnerabilities. At the other end of the exploitability scale are vulnerabilities that require administrator permission levels which account for a total of 30.71% of reported vulnerabilities.
Permit levels required for operations
Vulnerabilities requiring administrator-level credentials accounted for the highest percentage of exploits, followed by cross-site request forgery (CSRF) with 24.74% of vulnerabilities. This is interesting because CSRF is an attack that uses social engineering to get a victim to click on a link from which the user’s permission levels are acquired. If they can trick an admin-level user into following a link, then they can assume that level of privileges on the WordPress website.
Below are the percentages of exploits sorted by roles required to launch an attack.
Ascending order of user roles for vulnerabilities
Author 2.19% Subscriber 10.4% Unauthenticated 12.35% Contributor 19.62% CSRF 24.74% Administrator 30.71%
Most common vulnerability types that require minimal authentication
Broken access control in the context of WordPress refers to a security flaw that can allow an attacker without the necessary permission credentials to gain access to higher credential permissions.
In the section of the report that analyzes the occurrences and vulnerabilities underlying reported unauthenticated or subscriber-level vulnerabilities (occurrence reports vs vulnerability in unauthenticated or subscriber+), WPScan breaks down the percentages for each type of vulnerability that is more common for the farms that are the easiest. to launch (because they require minimal or no user credentials authentication).
The WPScan threat report noted that breached access control accounts for a whopping 84.99% followed by SQL injection (20.64%).
The Open Worldwide Application Security Project (OWASP) define broken access control as:
“Access control, sometimes called authorization, is how a web application grants access to content and features to some users and not to others. These checks are performed after authentication and govern what “authorized” users can do.
Access control seems like a simple problem, but it’s insidiously difficult to implement correctly. A web application’s access control model is closely tied to the content and features offered by the site. Additionally, users can belong to multiple groups or roles with different abilities or privileges.”
SQL injection, at 20.64%, represents the second most common type of vulnerability, which WPScan called “high severity and risk” in the context of vulnerabilities that require minimum authentication levels because attackers can access and/or manipulate the database that is the database. heart of every WordPress website.
Here are the percentages:
Broken Access Control 84.99% SQL Injection 20.64% Cross-Site Scripting 9.4% Unauthenticated Arbitrary File Upload 5.28% Sensitive Data Disclosure 4.59% Insecure Direct Object Reference (IDOR) 3 .67% Remote code execution 2.424% Other 1.424%
Vulnerabilities in the core of WordPress itself
The vast majority of vulnerability issues were reported in third-party plugins and themes. However, in 2023 there were a total of 13 reported vulnerabilities in WordPress core itself. Of the thirteen vulnerabilities, only one was rated as a High Severity threat, which is the second highest level, with Critical being the highest level vulnerability threat, a scoring system that maintains the Common Vulnerability Scoring System (CVSS).
The core WordPress platform itself is held to the highest standards and benefits from a worldwide community that is vigilant in discovering and fixing vulnerabilities.
Website security should be considered as technical SEO
Site audits usually don’t cover website security, but in my opinion every responsible audit should at least discuss security headers. As I’ve been saying for years, website security quickly becomes an SEO issue once a website’s ranking starts to disappear from the search engine results pages (SERPs) due to a vulnerability That’s why it’s critical to be proactive with website security.
According to the WPScan report, the main entry point for hacked websites was leaked credentials and weak passwords. Ensuring strong password standards and two-factor authentication is an important part of every website’s security posture.
Using security headers is another way to help protect against Cross-Site Scripting and other types of vulnerabilities.
Finally, a WordPress firewall and website hardening are also useful proactive approaches to website security. I once added a forum to a new website I built and within minutes it was immediately attacked. Believe it or not, virtually every website in the world is attacked 24 hours a day by bots looking for vulnerabilities.
Read the WPScan report:
WPScan 2024 Website Threat Report
Featured image by Shutterstock/Ljupco Smokovski
[ad_2]
Source link




