Proofpoint researchers revealed more technical details about SocGholish, the malware variant they identified earlier this monthhighlighting their remarkable tactics that differ from traditional fishing campaigns.
According to a Proofpoint blog entry On Tuesday, SocGholish deviates from the norm by forgoing all the classic staples of modern fishing, such as instilling a sense of urgency, promises of rewards and misdirection. Instead, researchers found that SocGholish is exploited in site-injection email campaigns, primarily targeting organizations with extensive marketing campaigns or strong search engine optimization.
“[SocGholish] it really is sophisticated. I don’t like to use the word “sophisticated” when it comes to threats in general, but this actor [along with] their development lifecycle and various techniques are really ahead of other actors,” said Andrew Northern, senior threat researcher at Proofpoint, during a virtual event on Tuesday.
Drew Schmitt, security management consultant and principal analyst at GuidePoint Security, expanded on this point, telling SC Media in an email that SocGholish had not been observed using this attack vector and its mail-based attacks before electronic combined with download-style infections “is unique in that it explicitly avoids having characteristics that the average user would be able to detect and identify.”
First test point he tweeted on the SocGholish attacks on November 2, revealing that the malware has infected more than 250 US news sites. The company said it observed intermittent injections at a media company that serves content via Javascript to its partners. The threat actor, tracked by Proofpoint as TA569, modified the codebase of the benign Javascript and used the media company to deploy SocGholish, which could lead to a dangerous supply chain attack.
Proofpoint researchers told SC Media that the threat actor is not targeting the media industry directly, but is using those companies as delivery mechanisms. The intended victims are the consumers who visit these sites.
“Actors are opportunistic and will inject scripts wherever they can: into landing pages, third-party style resources, crawlers and scripts,” said Sherrod DeGrippo, vice president of threat detection research at Proofpoint. “They rely on the engaging entity being a legitimate organization and natural email traffic, such as newsletters, marketing efforts and newsletters, to drive traffic to these sites. In the case of online media, articles are often “they optimize for search engines, so ad hoc search would also lead potential victims to compromised sites.”
Matthew Fulmer, cyber intelligence engineering manager at Deep Instinct, added that SocGholish is notable because it’s not just an attack to gain credentials, but to gain persistence and lateral movement to remove additional malware payloads, which could include ransomware or other threats. .
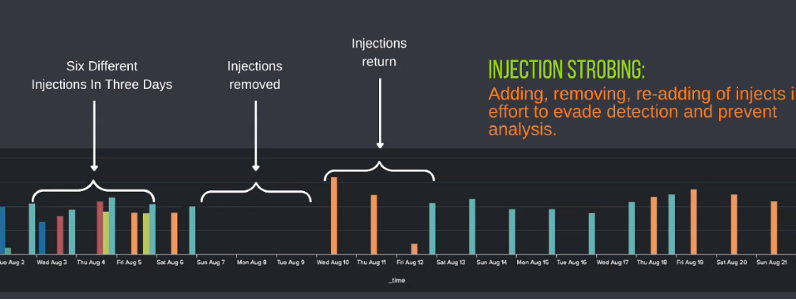
Tuesday’s virtual session also highlighted how the group has applied stroboscopic injection, a technique that adds, removes and re-adds injections to avoid detection and prevent analysis.
TA569 maintains control over injected hosts (Credit: Proofpoint/Andrew Northern)
Northern said one of the potential motivations for TA569 to manipulate injected hosts is to confuse incident responders and prevent them from analyzing the malware. He said it could also be the result of attackers meeting their quota to deliver other payloads.
“There are many reasons why these injections can work, but the key here is that you don’t learn to tell it’s a false positive,” Northern said. “If you’re a responder and you say this is a false positive because you can’t find it, you discount the next steps to check that host for lateral moves.”
To defend against threat actors, Northern suggested that organizations enable WMI, subscription, consumer, and trigger logging and centralize these logs to monitor post-exploit activity.
Schmidtt warned that the SocGholish malware detection is a stark reminder of the threat of supply chain attacks.
“Although not seen as frequently as other attack mechanisms, the controlled use of a supply chain compromise, as recently observed by SocGholish, may be indicative of an even more focused approach to exploit supply chain attacks in general,” Schmitt said.
[ad_2]
Source link




