A Reddit user looking to download and install the free image editor GIMP has discovered a malware campaign that uses Google contextual search ads to trick unsuspecting users into installing the RedLine Stealing Malware. The user who discovered and reported this campaign almost fell for it himself, until Windows Defender made him think twice before running the executable he downloaded after clicking the first GIMP search result. As it turned out, the main search result was an ad that sent the user to a malicious clone of the official GIMP website, even though the result appeared as “gimp.org”, which is the domain name of the official website
One of the methods threat actors use to distribute malware is known as SEO poisoning, with SEO for search engine optimization. SEO poisoning takes advantage of various SEO techniques, such as stuffing a web page’s source code with tons of keywords, to increase the ranking of a malicious website in search results. If a threat actor manages to play with the search results in this way and place a malicious website near the top of the search results, users can visit the malicious website and download malware without realizing it. However, this newly discovered malware campaign shows that threat actors don’t need to use SEO tactics to place a malicious website at the top of search results if they can instead pay Google to do for them
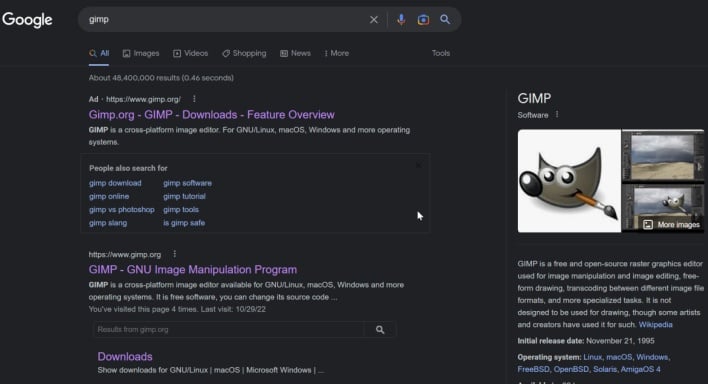
 Google search results show malicious ad as top result (click to enlarge) (source: ZachIngram04)
Google search results show malicious ad as top result (click to enlarge) (source: ZachIngram04)
Before reporting the ad to Google as malicious, a Reddit user found that a Google search for “gimp” returned a set of lists topped by what appears to be an official ad for the free image editor . The ad even contains the domain name of the official website, gimp.org, as well as the same description as the official website listing directly below the ad.
However, instead of sending users to the official GIMP website, the ad sent users to a malicious copy of the GIMP website with a misspelled domain name. The contextual ad was most likely sent to Google by a threat actor, rather than someone from the GIMP development team.
Initially, users clicking the download button on the malicious website were sent to Dropbox to download an executable file called “Setup.exe”. After uploading this file to VirusTotal and discovering that it contained malware, the Reddit user who discovered the scheme reported the ad to Google as malicious, asking the company to remove the ad .
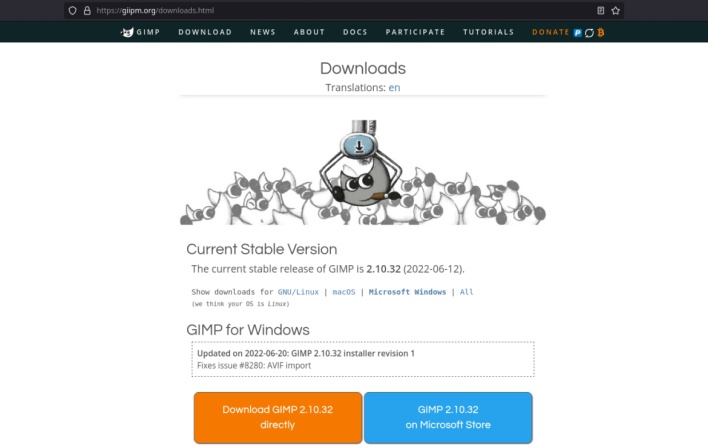 The malicious download page looks almost identical to the legitimate download page (click to enlarge)
The malicious download page looks almost identical to the legitimate download page (click to enlarge)
The threat actor behind the malware campaign simply responded by sending another visually identical ad redirecting users to a malicious clone of the GIMP website on a domain name with a different spelling of gimp. org. Instead of sending users to Dropbox, the download button on this second malicious website sends users to a download page that looks almost identical to the legitimate download page on the official GIMP website.
The GIMP for Windows download buttons on this webpage obtain the malicious Setup.exe file from the Discord Content Distribution Network (CDN), while redirecting users to the tutorial page on the official website of GIMP. This updated download process looks more reliable than a random Dropbox download page, but the downloaded file is just as malicious. Running this executable installs the RedLine stealing malware, which collects valuable information from infected systems and then uploads it to a command and control (C2) server managed by threat actors.
To avoid being tricked by a scheme like this, users should check domain names in the address bar before downloading software to make sure they’re visiting legitimate websites. Many software developers also provide hash values on their websites, which users can check against the hash value of the downloaded files before running them to verify the integrity of the downloaded files. In the case of this fake GIMP campaign, the threat actor simply copied the official GIMP website almost verbatim, leaving the correct hash value on the download page. Anyone who has checked the malicious executable against the hash value listed on the website will find that the sums do not match, indicating that the file is not legitimate. Checking hash values may seem like a tedious extra step, but it can actually save you from unknowingly installing malware on your systems.
[ad_2]
Source link




