Cybercriminals continue to take advantage of users looking for cracked software by directing them to fraudulent websites that host weaponized installers that deploy malware called NullMixer in compromised systems.
“When a user extracts and runs NullMixer, it drops a series of malware files onto the compromised machine,” cybersecurity firm Kaspersky said in a report on Monday. “It drops a wide variety of malicious binaries to infect the machine, including backdoors, bankers, downloaders, spyware and many others.”
In addition to siphoning credentials, address, credit card data, cryptocurrencies, and even session cookies from Facebook and Amazon accounts, what makes NullMixer insidious is its ability to download dozens of of Trojans at once, significantly expanding the scale of infections.
Attack chains usually start when a user tries to download cracked software from one of the sites, which leads to a password-protected archive containing an executable file that in turn drops and launches a second binary of configuration designed to deliver a series of malicious files.
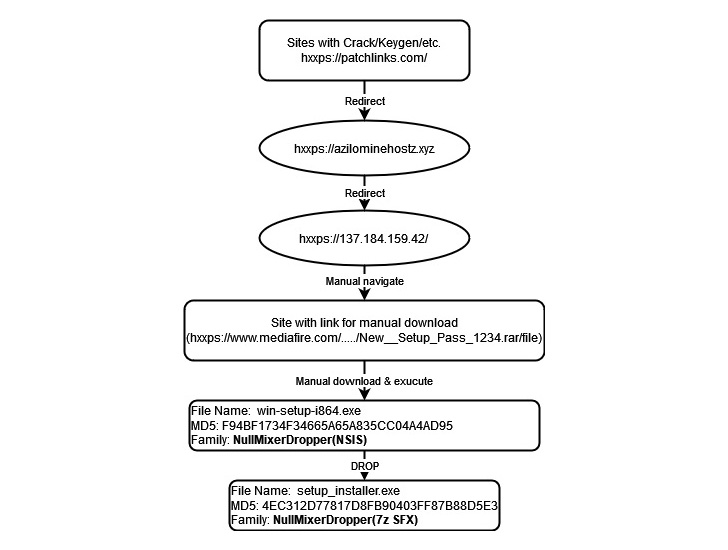
These malicious websites take advantage of search engine optimization (SEO) poisoning techniques such as keyword stuffing to display prominently in search engine results. Similar tactics have been adopted by the actors behind the GootLoader and SolarMarker campaigns.
NullMixer was last month linked to the distribution of a rogue Google Chrome extension called FB Stealer, which is capable of stealing Facebook credentials and replacing the search engine.
Some of the other notable malware families distributed by the dropper include DanaBot and a number of information-stealing malware such as ColdStealerPseudoManuscrypt, Raccoon Stealer, Redline Stealer and Vidar.
Trojan downloaders such as FormatLoader, GCleaner, LegionLoader (aka Satacom), LgoogLoader, PrivateLoader, SgnitLoader, ShortLoader, and SmokeLoader have also been deployed via NullMixer, as well as the C-Joker cryptocurrency wallet stealer.
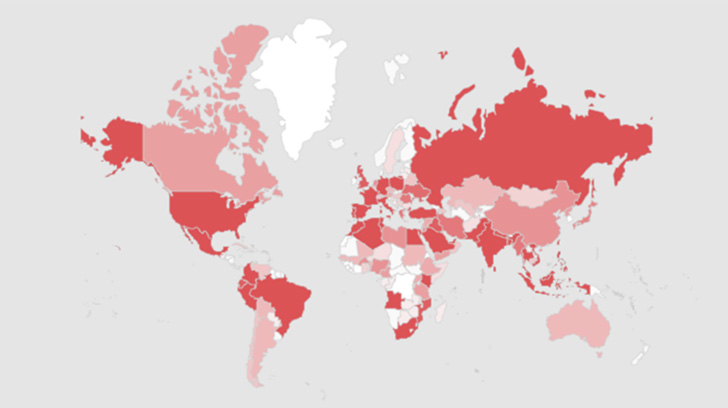
Kaspersky said it blocked attempts to infect more than 47,778 victims worldwide, with the majority of users located in Brazil, India, Russia, Italy, Germany, France, Egypt, Turkey and the US. a known group.
The latest findings are another indication that malware and unwanted apps are increasingly being spread through pirated software. It is also recommended to regularly check online accounts for unknown transactions.
“Any download of files from unreliable resources is a real game of roulette: you never know when it will trigger and what threat you will have this time,” said Kaspersky researcher Haim Zigel. said. “By receiving NullMixer, users receive multiple threats at once.”
[ad_2]
Source link






